
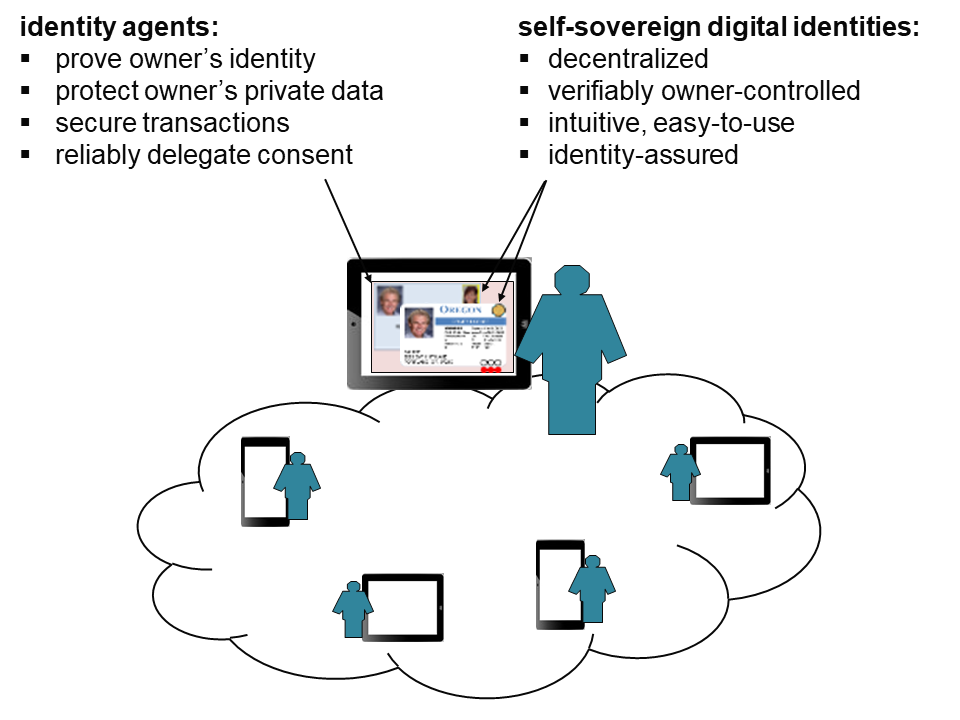
Our architecture is comprised of inter-operating identity agents installed on personal devices that deploy and control “self-sovereign” digital identities on behalf of the device owner (see videos).
When creating our identity architecture we analyzed the shortcomings of existing technologies, the capabilities of personal devices, the benefits of decentralizing identity, and the principles of privacy by design.
The architecture assures relying parties that digital identities reliably characterize the person or entity they purport to represent. They are considered “self-sovereign” because they are tightly bound to their owners.
Each digital identity has a master copy, called the “sovereign image“, which is solely controlled by its owner. An owner can use her identity agent to present the public copy of a selected identity of the owner to prove who she is. Other parties cannot use the public copy of a self-sovereign digital identity to impersonate the owner.
Identity agents also leverage their owners’ digital identities to protect their private data and transactions, reliably delegate consent, securely exchange identities, and register identities that can be verified by other parties.
Owners can use their identity agents to elevate identity assurances by affixing identity attestations to the digital identities of other owners using “digital seals“. Such attestations cannot be repudiated.