Users, providers and system admins have identity agents installed on their Internet devices, for example, on their smart phones, tablets, laptops, and servers. Identity agents control digital identities for their owners and enable them to prove who they are, control disclosure, secure transactions, proof/attest identities, and delegate consent. Identity agents tightly bind the owner to her device, identities, private data and consent tokens by encapsulating the owner’s authentication data (e.g. biometrics).
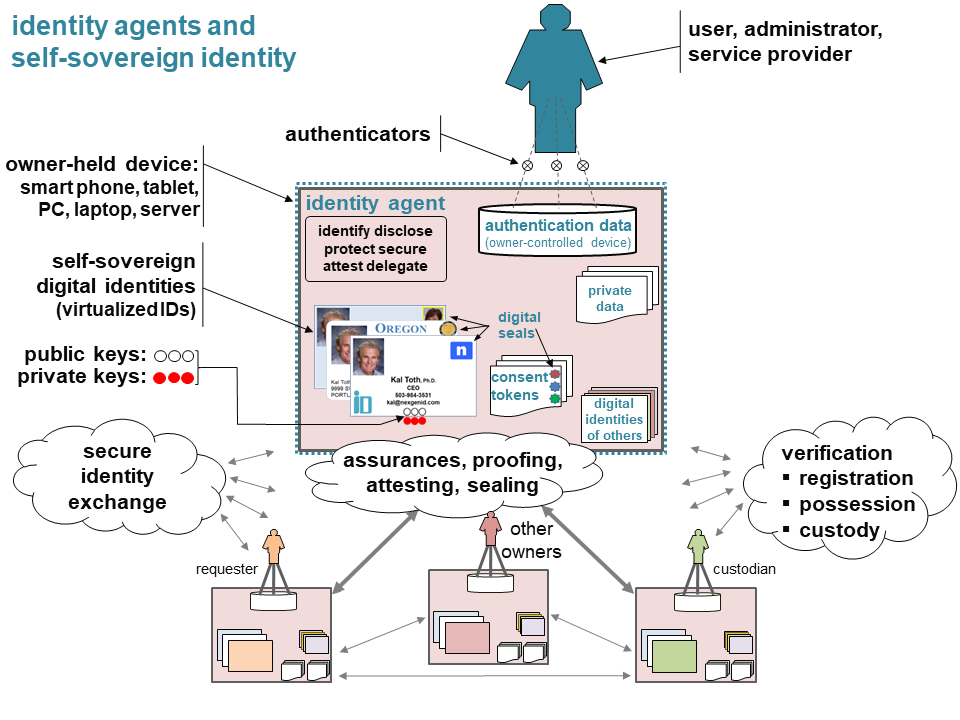
Identity agents use a digital identity model to virtualize identifying credentials for the owner and use virtualized notarizing seals to cryptographically bind owner identities to digital identities, consent tokens and other artifacts. Digital identities are allocated multiple public/private key-pairs.
Identity agents can securely exchange digital identities online or by device-to-device transfer. They can also use a proof-of-existence registry and conduct proof-of-possession and proof-of-custody challenges to verify digital identities. Once exchanged, the allocated crypto keys can be used to secure and seal transactions and consent tokens.
Ordinary users and designated parties can use their identity agents to elevate assurances by proofing, attesting and sealing the identities of other owners. Digital seals cannot be repudiated since they cryptographically bind the identities of owners to the attestations they make.
When delegating consent, the resource owner, resource custodian and the requester use digital seals to affix commitments to consent tokens that they cannot deny.