Agent-Based Digital Identity Architecture
Problems — Analysis — Solution — Adoption
Problems Plaguing the Web
The Internet lacks an identity layer for specifying and verifying user identity. PKI, HTTPS and SSL/TLS have reliably secured online transactions for decades. But user identity, privacy, and ease-of-use have been neglected. The Internet is supported by a patchwork of identity and authentication schemes relying on browsers and passwords. Browsers do not explicitly identify users and can be shared. Browsers generally have software bloat rendering them vulnerable to hacking. Passwords can be “phished”, are often weakly specified, reused, and can be cracked. Password compromise is the most common cause of impersonation and breaches. Meanwhile, users are frustrated maintaining countless passwords and online profiles over all the providers they use. User-asserted identifiers, online passwords, second factors and biometrics can be relatively straight-forward to use but are not intuitive and do not prove who users are. These issues continue to undermine the web economy.
Fixing these Problems
Digital Identity: Users are ideally-positioned to specify and verify digital identities since they hold their foundational identifying documents and know the attributes of family, friends, co-workers, and associates.
Decentralizing: Shifting responsibility and control over identity from providers to users puts digital identity squarely in the hands of users, off-loads providers, and globally disperses the attack surface.
vCard 4.0: Exploiting this standard gives digital identities the “look and feel” of credentials in one’s wallet and makes them much more intuitive and meaningful to use than passwords.
Biometrics: Using biometrics to bind users to digital identities mitigates loss and tampering risk. Captured biometric minutia should not be disclosed to others since such private data can be misused and abused.
Cryptography: Digital identities integrated with elliptic curve cryptography are much harder to phish and break than remote access passwords. Digital identities with integrated cryptographic keys can be used to mutually identify and authenticate users across multiple providers, secure transactions and privacy, and cryptographically bind users to digital identities, documents and tokens.
Identity Validation: Credit cards and other such credentials can be used to validate digital identities. Credit card data validating a “Card Not Present” (CNP) transaction can be used to validate the identifying attributes of a user’s digital identity. Similarly, contactless credit cards read via Near Field Communications (NFC) technology can be used to validate a user’s digital identity.
Identity-Proofing: Online and in-person identity-proofing requires the user to submit her digital identity and identifying data to a 3rd party (identity proofer) who uses the identifying data to determine if the digital identity faithfully identifies her.
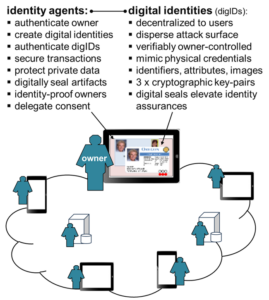
Identity Agents: implement the fixes for owners thereby resolving the problems. Software complexity (“bloat”) is minimized; trustworthy authenticators locally bind owners to identity agents; and authentication minutia, digital identities and private data are reliably safeguarded.
Solution Synopsis
The architecture is comprised of identity agents deploying digital identities enabling owners to mutually identify, authenticate, and secure transactions and private data.
Solution: Better than your Wallet
Technology Adoption
The architecture‘s critical features are specified in four US patents, one patent application, and eleven conference papers and journal publications. A progressive roadmap anchored by focused initial projects is planned. To facilitate technology adoption, ease-of-use, privacy, and security are baked in. A proof-of-concept prototype has been developed to validate the solution. The architecture is comprised of identity agents deploying digital identities (“sovereign copies”) that “look & feel” like physical credentials; have three (3) long-term elliptic curve key-pairs; and are verifiably owner-controlled (self-sovereign). Derived “public copies” are securely exchanged user-to-provider via HTTPS and user-to-user via ECDHE.
Artificial Intelligence (AI)
Going forward, it is expected that identity agents will be able to exploit artificial intelliegence (AI) to help owners avoid, detect, and prevent impersonation and man-in-the-middle (MITM) attacks, as well as help them decide which digital identities to select and how much private information to disclose.
