
Agent-Based Digital Identity Architecture
Problems — Analysis — Solution — Adoption
Problems Plaguing the Web
Today’s web is a server-centric patchwork of schemes unable to distinguish impersonators from reliable sources. The apparent root cause is that the Internet lacks an identity layer capable of reliably identifying users when required. The Public Key Infrastructure (PKI) has reliably secured service providers for decades. However, the identity, privacy and security needs of ordinary users have been neglected. Biometric authenticators and second factors have strengthened user-to-provider bindings, but reliable methods for users digitally identifying themselves when needed are not available. Financial, government and defense sector organizations have instituted various (non-standard) procedures for identity-proofing users and issuing authenticating credentials. Meanwhile, social networks and service providers gather little or no evidence validating identifying information asserted by users. Self-asserted identity does not prove who you are. Users and providers are frustrated maintaining countless passwords, resetting them, and keeping online profiles current. Passwords are often weakly specified and routinely reused across providers and users are obliged to cope with harmful scams daily. Unsurprisingly, impersonators, hackers and fraudsters continue to exploit these many identity-related deficiencies.
Analysis
Judicious decentralizing of control over digital identity from service providers to users is mutually benefical. Users can keep their digital identities current and consistent across relying parties and limit what identifying information is disclosed. This offloads service providers. Decentralizing control over identity requires users to be strongly bound to their digital identities possibly by way of biometics. Providing digital identities that mimic credentials used in the physical world facilitates intuitive ease-of-use as long as leaked or stolen copies cannot be used to impersonate. Established cryptographic methods (elliptic curve, ECDSA, ephemeral (short-term) keys, Diffie-Hellman (ECDHE), SHA-256, etc.) can overcome the weaknesses and frustrations of using remote access passwords. Identity-proofing conducted by known and qualified third parties can elevate identity assurances associated with digital identities specified and controlled by users.
Proposed Solution
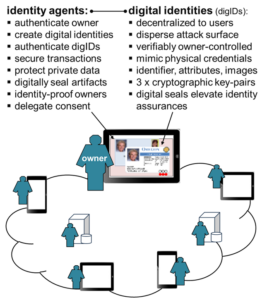
The architecture is comprised of identity agents deploying digital identities for owners who can use them to mutually identify, mutually authenticate, and secure messages, transactions, and private information.
Solution: Better than your Wallet
Technology Adoption
The architecture‘s critical features are specified in four US patents, one patent application, and eleven conference papers and journal publications. A progressive approach anchored by a focused initial project is planned. To facilitate technology adoption, usability, privacy, and security are baked into the solution. A proof-of-concept prototype has been developed to validate the architecture. The architecture is comprised of identity agents deploying digital identities that “look and feel” like credentials in one’s wallet; include three (3) long-term elliptic curve key-pairs; and are verifiably owner-controlled (“self-sovereign”). Identity agents can create and use digital identities enabling owners to mutually identify, authenticate, collaborate, digitally seal artifacts, identity-proof other owners, delegate consent, and protect private information.
Possible Application of AI
Going forward, identity agents should be able to exploit artificial intelliegence (AI) to help owners avoid, detect, and prevent impersonation, phishing, and man-in-the-middle (MITM) attacks. Owner’s will be able to optimize the decisions they make when selecting digital identities and disclosing private information.